Security researcher highlights macOS remote exploit w/ custom URL schemes<div class="feat-image">
</div><p>Security researcher
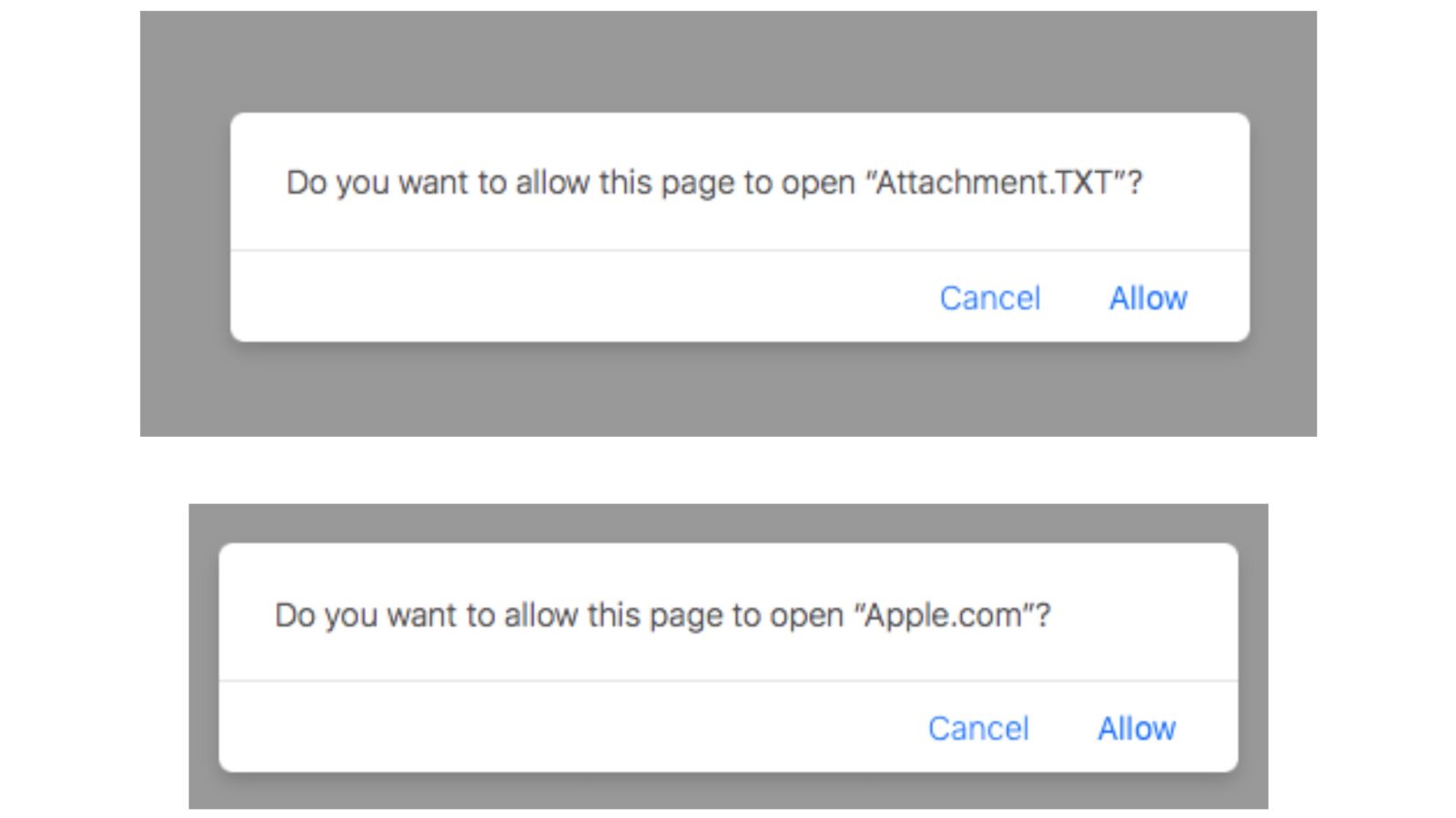
Patrick Wardle is out with a close look at a how macOS users can be remotely targeted using document handlers and custom URL schemes – which is behind the “Do you want to allow” popup seen in the above screenshot.</p>
<p> <a href="
https://9to5mac.com/2018/09/04/security-researcher-highlights-macos-remote-exploit-w-custom-url-schemes/#more-549890" class="more-link">more…[/url]</p><div class="feedflare">
<img src="[url]http://feeds.feedburner.com/~ff/9To5Mac-MacAllDay?i=hbklQHjixZY:1cengqpl8KM:D7DqB2pKExk" border="0"></img>[/url]
</div><img src="
http://feeds.feedburner.com/~r/9To5Mac-MacAllDay/~4/hbklQHjixZY" height="1" width="1" alt=""/>
Source:
Security researcher highlights macOS remote exploit w/ custom URL schemes