M1 MacBook Air Out of Stock at Walmart as Lower-Cost MacBook NearsApple's older MacBook Air with the M1 chip is now out of stock on Walmart's website in the U.S., amid rumors of a new lower-cost MacBook coming soon.
<div class="center-wrap">
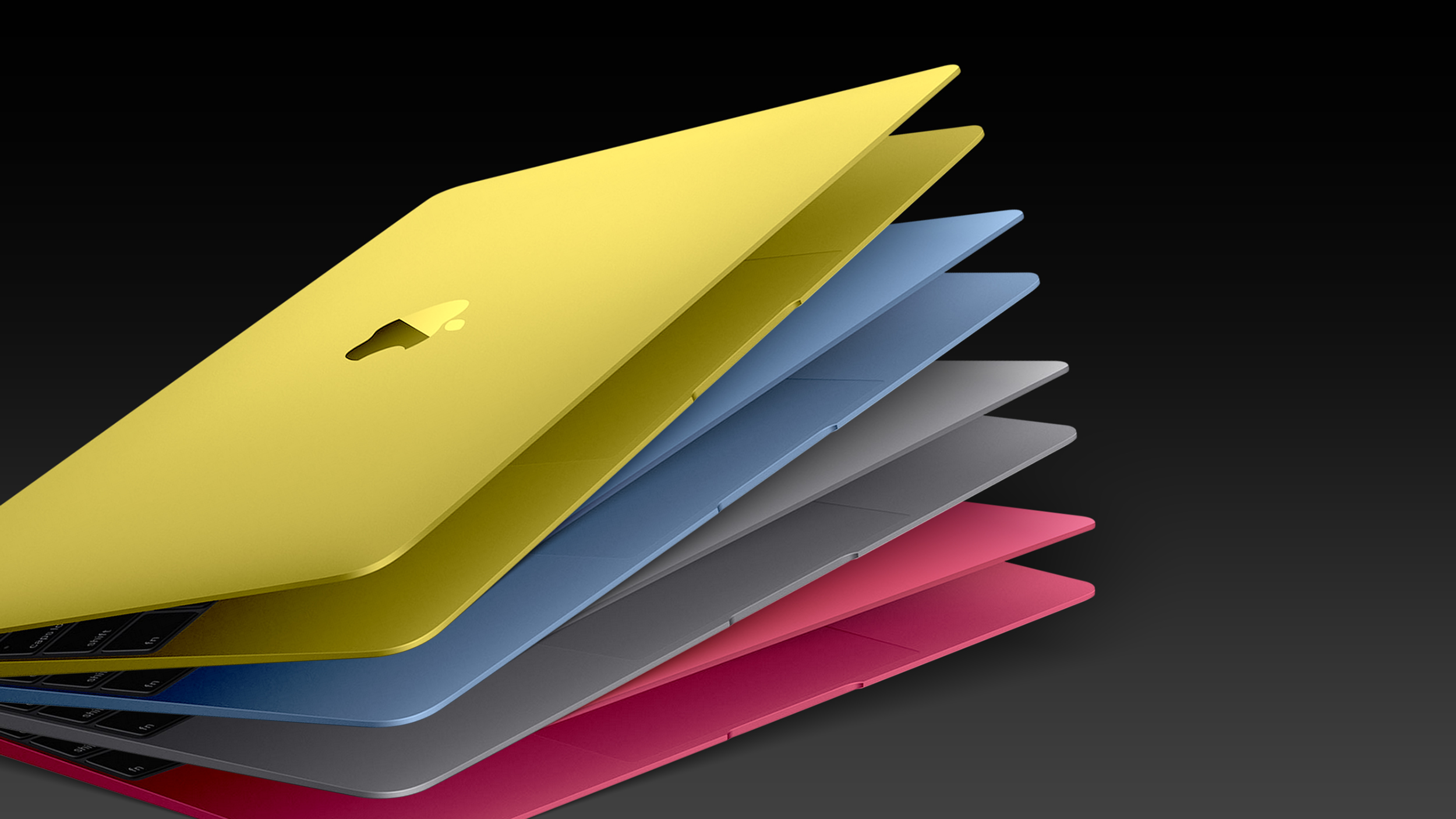 A colorful MacBook (concept)
A colorful MacBook (concept)</div>
Walmart first began selling the MacBook Air with the M1 chip
for $699 in March 2024. The price later dropped to
$649,
then to $599, and briefly to
as low as $549 during a Black Friday sale last year. However, we just noticed that it has been out of stock
for a while now, and there is no indication if it will ever be returning.
Apple first released the MacBook Air with the M1 chip in November 2020, as one of the first Macs with an Apple silicon chip, instead of an Intel processor. The configuration being sold by Walmart for as low as $549 included 256GB of storage and 8GB of RAM. They were new-in-box units, not refurbished or open-box models. Walmart's website continues to offer refurbished units from "trusted sellers" for as low as $449.
Apple
discontinued the MacBook Air with the M1 chip in 2024, after it launched models with the M3 chip, and it has since updated the MacBook Air with the M4 chip. Prior to being discontinued, the model with the M1 chip was being sold for a starting price of $999 brand new, but Amazon sometimes offered it on sale for $749 to $899.
The laptop going out of stock at Walmart could be a hint.
Apple
plans to release a lower-priced MacBook with a version of the iPhone 16 Pro's A18 Pro chip
as early as the first week of March, according to several reports and leakers. This would be an all-new model positioned below the MacBook Air in the Mac lineup, and it would mark a revival of the "MacBook" brand (with no "Air" or "Pro" designation).
Apple supply chain analyst Ming-Chi Kuo was first to reveal that Apple is allegedly planning a more affordable MacBook. Last year, he said the laptop would have around a 13-inch display and come in fun colors, like
green, blue, pink, and/or yellow. A few rumors have specifically said it will have a 12.9-inch screen.
The lower-cost MacBook could have a lot in common with the
discontinued 12-inch MacBook, including an ultra-thin and lightweight design. However, that model was powered by Intel processors. Apple stopped selling the 12-inch MacBook in July 2019, so there has been a long wait for a similar model powered by Apple silicon.
In the iPhone 16 Pro, the A18 Pro chip has a 6-core CPU and a 6-core GPU. The chip's multi-core performance is similar to the M1 chip, so this new MacBook could effectively be a replacement for the MacBook Air with the M1 chip, and that could explain why it is finally out of stock at Walmart ahead of the lower-cost MacBook launching.
Skyrocketing DRAM and NAND storage chip prices may have been a factor too, though.
With the A18 Pro chip, the lower-cost MacBook might have only 8GB of RAM, whereas all current MacBook Air and MacBook Pro models start with at least 16GB of RAM. The chip also lacks Thunderbolt support, so the new MacBook would likely be equipped with regular USB-C ports, with slower data transfer speeds and external display limitations.<div class="linkback">Related Roundup:
MacBook Air</div><div class="linkback">Tag:
MacBook (A18 Pro)</div><div class="linkback">Buyer's Guide:
13" MacBook Air (Don't Buy)</div><div class="linkback">Related Forum:
MacBook Air</div>
This article, "
M1 MacBook Air Out of Stock at Walmart as Lower-Cost MacBook Nears" first appeared on
MacRumors.comDiscuss this article in our forums
Source:
M1 MacBook Air Out of Stock at Walmart as Lower-Cost MacBook Nears