AirTags can be weaponized by injecting code; Apple says fix on the way<div class="feat-image">
</div>
<p>A <a href="
https://9to5mac.com/guides/security/" target="_blank" rel="noreferrer noopener">security[/url] researcher has shown that <a href="
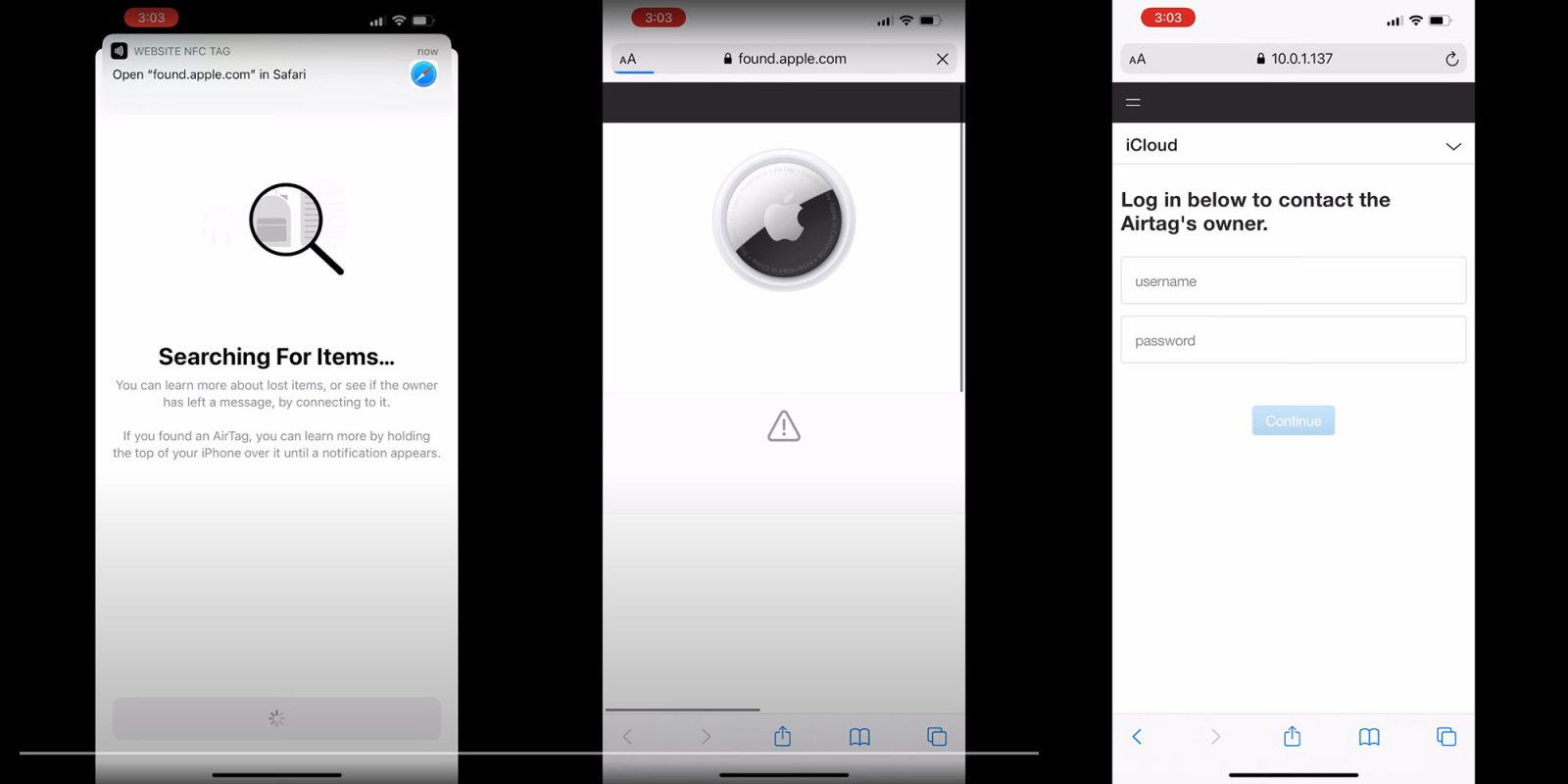
https://9to5mac.com/guides/airtag/" target="_blank" rel="noreferrer noopener">AirTags[/url] can be weaponized by injecting code into the phone number field before placing it into Lost mode and dropping it in strategic places. <a href="
https://9to5mac.com/guides/aapl/" target="_blank" rel="noreferrer noopener">Apple[/url] has confirmed the finding.</p>
<p>When someone finds the AirTag and scans it, they will be redirected to the website of the attacker’s choice, which could include a fake <a href="
https://9to5mac.com/guides/icloud/" target="_blank" rel="noreferrer noopener">iCloud[/url] login to report the find … </p>
<p> <a href="
https://9to5mac.com/2021/09/29/airtags-can-be-weaponized/#more-757466" class="more-link">more…[/url]</p>
<p>The post <a rel="nofollow" href="
https://9to5mac.com/2021/09/29/airtags-can-be-weaponized/">AirTags can be weaponized by injecting code; Apple says fix on the way[/url] appeared first on <a rel="nofollow" href="
https://9to5mac.com">9to5Mac[/url].</p><div class="feedflare">
<img src="[url]http://feeds.feedburner.com/~ff/9To5Mac-MacAllDay?i=MVWwH9J275c:SFDrUoA43A8:D7DqB2pKExk" border="0"></img>[/url]
</div><img src="
http://feeds.feedburner.com/~r/9To5Mac-MacAllDay/~4/MVWwH9J275c" height="1" width="1" alt=""/>
Source:
AirTags can be weaponized by injecting code; Apple says fix on the way